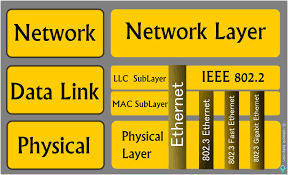
Most of the protocols using the data link layer and local broadcast addresses are nonroutable, which means you can only evaluate them from the local
Tag: Firewalls
TLS Security (Part I)
I. What is TLS? Before getting into TLS security, let’s first talk about encryption. It can generally be applied at different levels, from encryption in
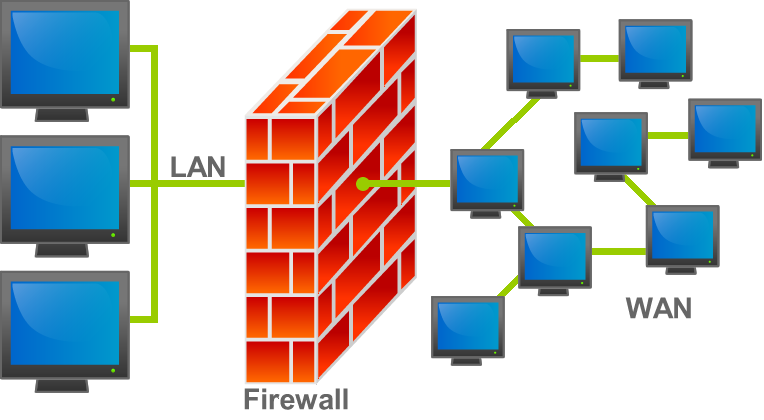
Firewalls Introduction
Firewalls can handle simple attacks pretty quickly. However, they can easily be tricked because of the nature of network traffic in which almost all network traffic is bi-directional, but stateless firewalls must decide on….