I/ 802.1X
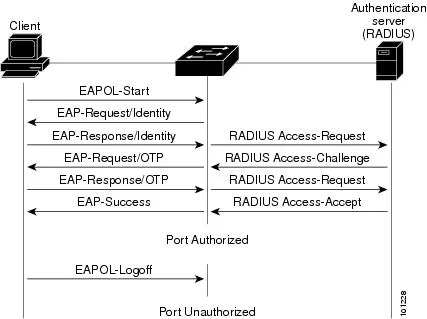
Port-based Network Access Control (PNAC) enables authentication of devices that connect to a local network. The below image illustrates the transmission of Extensible Authentication Protocol (EAP) messages between the supplicant, authenticator, and authentication server. Devices that haven’t been authenticated cannot access the network, but they have the ability to initiate EAP exchanges with the RADIUS server located in the backend.
The majority of 802.1X implementations have the capability to use the EAP methods that are commonly found in the table below. Among these methods, EAP-MD5 presents a challenge because it is susceptible to offline password cracking through brute-force methods. On the other hand, EAP-TLS and Protected EAP (PEAP) offer authentication and transport security through TLS, which helps reduce the risk of credential exposure. Nevertheless, in all cases, the supplicant identity is revealed in the EAPOL start message in plain text.
| Method | Authentication process |
| EAP- MD5 | The authentication process for EAP-MD5 involves the authentication server sending a challenge to the supplicant. In response, the supplicant generates an MD5 hash by using an identifier, challenge value, and user password, which is then sent back to the server. The server also performs the same calculation and if the hashes match, the supplicant is successfully authenticated. |
| EAP- TLS | A TLS session is created between the authentication server and the supplicant. During this process, the supplicant verifies the X.509 certificate of the authentication server, and conversely, the server verifies the supplicant’s certificate. This mutual authentication is achieved using certificates, thereby eliminating the need for passwords. |
| PEAP | The supplicant and authentication server create an authenticated TLS tunnel. To authenticate the supplicant using the user’s credentials (i.e., username and password), the MS-CHAPv2 challenge/response mechanism is utilized over TLS. |
Here are some of the attack tactics that can use to against 802.1X implementations:
- Active brute-force password grinding via EAP
- Attacking the RADIUS server with malformed EAP content
- EAP message capture and offline password cracking (EAP-MD5 and PEAP)
- Forcing EAP-MD5 authentication to bypass TLS certificate validation
- Injecting malicious network traffic upon authenticating using a hub or similar
II/ 802.1D STP
The Spanning Tree Protocol (STP) is a technique employed to ensure that network topologies remain free of loops. By using Bridge Protocol Data Unit (BPDU) frames, switches can organize themselves by designating redundant uplink ports as “blocking” in order to prevent loops from forming.

Port states within STP networks
| State | Description |
| Disabled | Electrically inactive until enabled |
| Blocking | Port discards all data except BPDU frames |
| Listening | Switch listens to BPDUs to build a loop-free tree |
| Learning | Switch builds a forwarding table using source MAC addresses of frames |
| Forwarding | Port becomes fully operational, forwarding traffic to/from the switch |
After choosing a root bridge, switches determine which ports will be root and designated ports. The root port is the one that offers the most optimal route to the root bridge, while the other ports are designated. If you want more information on the BPDU election process and port configuration, you can refer to Kevin Lauerman and Jeff King’s paper, which includes several in-depth topology diagrams and low-level examples.
1. Monitoring BPDUs
BPDU frames are captured and displayed within the Yersinia STP protocol view: “https://github.com/tomac/yersinia“
2. Root bridge takeover
To connect two switches in a given environment, you can utilize Ettercap to create a bridge between them. Additionally, you can use Yersinia to transmit customized BPDU frames via each interface.
Note: To disrupt communication between other switches in a network, you can carry out a CAM table overflow attack using macof. This will cause switches to broadcast frames to all ports, allowing you to intercept and analyze the traffic.
Our other posts: