I. LM/NTLM Hashes
1. LM
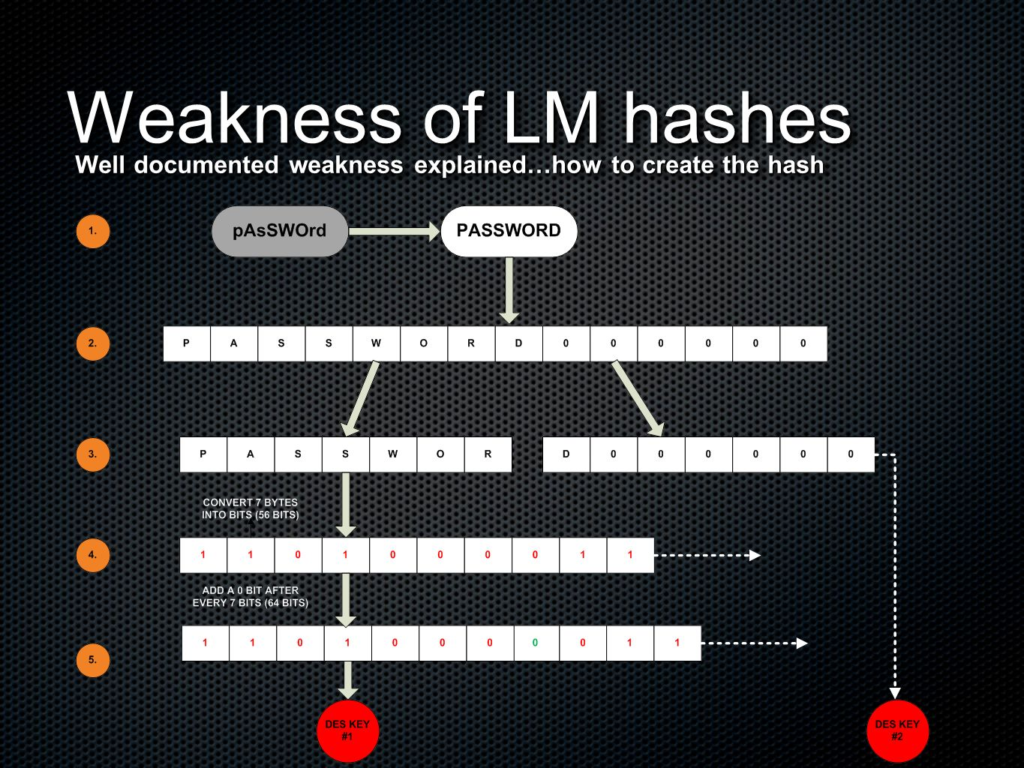
LAN Manager hash is the oldest password hash used by Windows and was introduced in 1980. It was used to store passwords on Windows system prior to Windows NT. Here is how the algorithm looks like:
- The user’s ASCII password is converted to uppercase
- This password is null-padded to 14 bytes
- The fixed length 14-byte password is split into two 7-byte halves
- Each of the two halves is used with the DES function to create two 8-byte cipher text values
- The two cipher text values are concatenated to form a 16-byte value, which is the LM hash
- No salt is used in the hash’s creation
Because of that, this hashing is easy to crack and should not be recommended to use anymore due to the following reasons:
- Maximum password length is only 14 characters
- Each lowercase character is converted to uppercase which means we have less possible combinations and it’s easier to crack the password
- By splitting the passwords in two halves we reduce the complexity of the password and it’s easier for cracking tools to guess the password
- There’s no random attribute added to the passwords, typically referred to as a salt which resulted in the possibility of rainbow table attack (pre-computing).
2. NTLM
NT LAN Manager (NTLM) is the Microsoft authentication protocol that was created to be the successor of the LM. This protocol uses the MD4 hash to create the hash based upon a series of mathematical calculations, and MD4 is stronger than DES. Some of the benefits that NTLM brings are:
- Longer passwords are possible
- Password are case sensitive
- No usages of password chunks

However, it’s essential to know that NTLMv1 hashes are commonly cracked, revealing the NT hash that was used to generate them. One of which is the rainbow tables attack which contains a list of known hashes exist for chosen NTLMv1 challenges, making it possible to obtain the hash in minutes.
NT Lan Manager or NTLM on Wikipedia
II. NTLMv2
In a domain joined environment, the default authentication mechanism is Kerberos. However, when Kerberos failed, Windows will fall back to NTLM authentication.
This can even happen between machines that are members of the same domain when all necessary conditions to use Kerberos are not in place. For example, Kerberos works with so-called services names (SPN). If we don’t have a name, Kerberos cannot be used. This is the case when we access a share on a file server by using the IP address of the server instead of its server name.
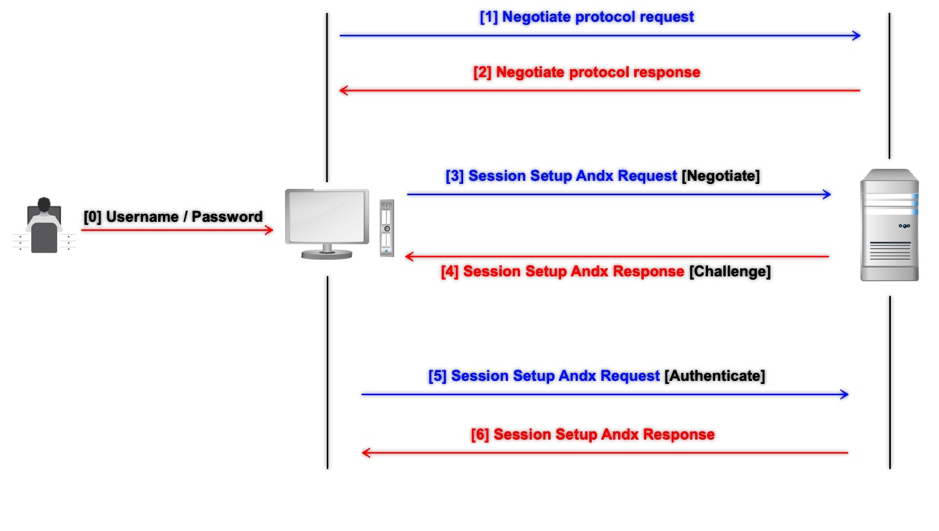
NTLM authentication is basically is a two party conversation: the client and the server which takes the following steps:
- Negotiate
- Challenge
- Response
The First step, the client sends a negotiate packet to the server to request the authentication. There are different parameters and versions for NTLM, and the version has to inform the server what it is capable of. This is done with a negotiated packet.
The following step at step 2, the server sends a challenge packet back to the client which includes a “nonce”. A nonce is a random number of 16 bytes.
Finally at step 3, the client sends the response back to the server which contains a calculated combination of the password and the nonce.
Using nonce allows the two parties to perform authentication without having to send the password in clear text over the network.
The server will check the credentials of the client by performing the same calculation as the client for the response, and if the response calculated by the server is the same as the response calculated by the client, then the client is authenticated to the server. The server needs the credentials of the client to perform the calculation. In Active Directory environment, the domain controller (DC) performs the validation of the response.
Explore more our posts: OSINT & Passive Recon, IDS and IPS, Firewalls, Data Security, Secure WordPress, Attack Vectors