I. What is an IDS?
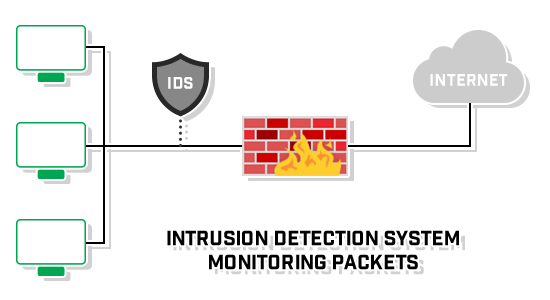
Before getting into to the details of each system, let’s talk about the definition of intrusion detection which is the process of monitoring activity on a host or on the network, identifying signs that might indicate an attempted or successful security breach.
An IDS or Intrusion Detection System monitors activity that is known or suspected to be malicious in its intent, raising alerts to a security or SOC teams to be analyzed.
We can think of IDS as an alarm system for identifying undesirable activity on your network or hosts if there is attack activity going on and in turn allowing the incident handler to respond to the activity according to the severity of the alerts. Organizations should not deploy IDS tools as a primary method of defense to protect their resources but should be utilized in conjunction with firewalls, AV, vulnerability assessment and management, as well as patch management tools to support a defense-in-depth posture instead.
There is one thing to remember that IDS is not a replacement for other security mechanisms that protect the network. Without comprehensive policies governing information security, and a clear understanding of what actions are needed to protect the corporate assets, an analyst won’t be able to react to alerts with any level of consistency.
II. What is IPS?
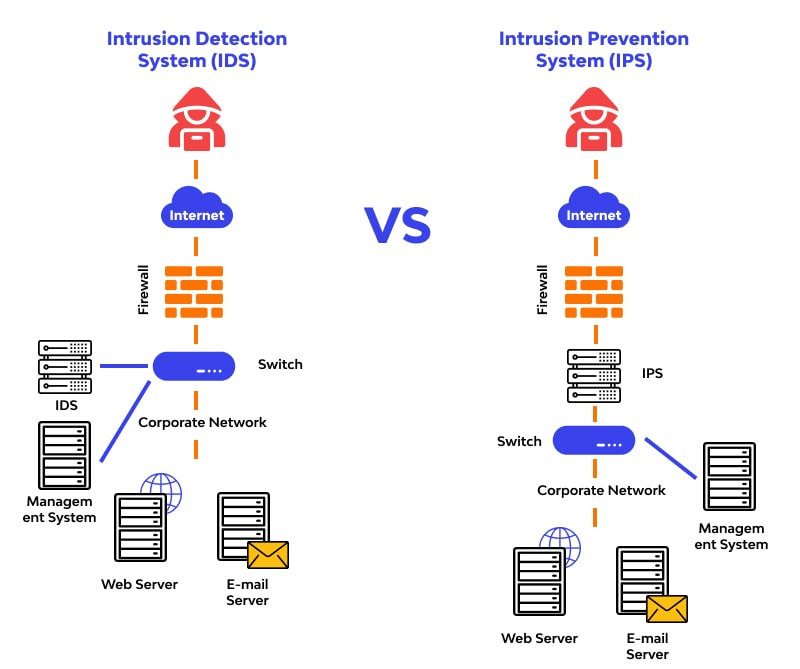
IPS or Intrusion Prevention System adds another layer of defensive measure to protect resources. While IDS reports only attacks against monitored systems and firewalls, which are utilized to permit or deny traffic based on source/destination IP addresses and ports, IPS attempts to stop attacks before they succeed.
How the IPS detects and stops the attack varies significantly between vendors, although each carries the same name of “intrusion prevention”.
IPS can be generally classified into two vectors: network-based (NIPS) and host-based (HIPS). NIPS products work at the network level, analyzing traffic whereas HIPS products are installed on individual hosts and stop attacks at the operating system or application level.
Unfortunately, IPS is not a one size fits all solution and no technology does, and thus the reason for defense-in-depth strategies. Deploying an IPS is not a replacement for patch management and system hardening but it provides a valuable asset which is time in which organizations using IPS are often able to extend the amount of time they have to deploy patches to resolve operating system and application flaws, potentially delaying the deployment of fixes until several patches have accumulated and a window for scheduled maintenance of equipment is available. Still, organizations should rely and implement defense-in-depth instead of relying on any particular technology or solution.
Explore our latest post: Firewall, Data Security, Secure WordPress, Nmap