I. Firewall Evasion
Nmap has a couple of options to bypass firewall rules and IDS/IPS such as decoys, packets fragmentation, scan delay and bad sum. In this post, we will go over the most practical and commonly used today. Before that, we’ll need to understand what firewall and IDS/IPS are? How do they work?
1. What is firewall?
A firewall a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules.
There are many types of firewalls and each of them has their own usage and purpose such as proxy firewall, statefull inspection firewall, unified threat management firewall, next-generation firewall, threat-focused NGFW and virtual firewall.
2. What is IDS/IPS?
IDS is Intrusion Detection System which monitors, analyzes and reports any potential attacks. On the other hand, IPS (Intrusion Prevention System) takes action if a potential attack has been detected based on pattern matching and signatures. For example, IPS can stop the service detection scan from Nmap.
II. Firewalls Rules Detection
- ACK Scan
You may notice that when a ports is filtered, Nmap will show opened|filtered which can have several reasons as the packets can either be dropped or rejected. The dropped packets are being ignored and Nmap does not receive any response from the target. On the contrary, Nmap will receive the RST flag in case of packets being rejected by the target. These rejected packages contain different types of ICMP error codes or nothing at all as:
- Net unreachable
- Net prohibited
- Host unreachable
- Host prohibited
- Port unreachable
- Proto unreachable
Let’s take a look at ACK scan with Nmap. The target will response with the RST flag if the port is opened or closed
sudo nmap -Pn -nvv <Target-IP> -p 21,22 -sA --disable-arp-ping --packet-trace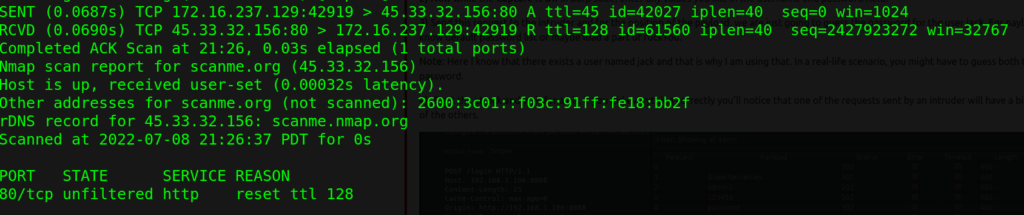
It’s a good practice to include the packet-trace switch which makes it easier for us to analyze the response.
2. Decoy scan
With this can, Nmap will generate many IP addresses along with our real IP. Moreover, Nmap can help us generate randomly by specifying the RND switch followed a semicolon and a number.
This scan type is used in case of administrator blocks IP addresses from certain subnets or regions.
sudo nmap -Pn -n -sS <Target-IP> -p 21,22 -D RND:10 --disable-arp-ping --packet-trace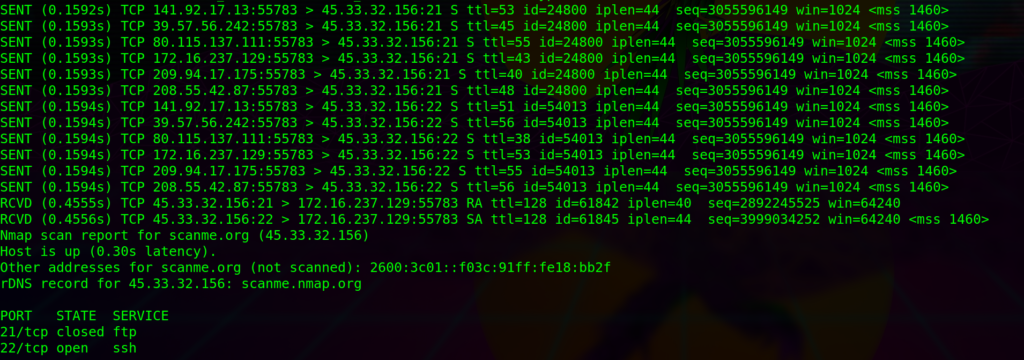
3. Fragmentation Scan
With this can, Nmap will split the packet into smaller pieces making it less likely detected by firewalls.
sudo nmap -Pn -n <Target-IP> -p 21,22 -f --disable-arp-ping --packet-trace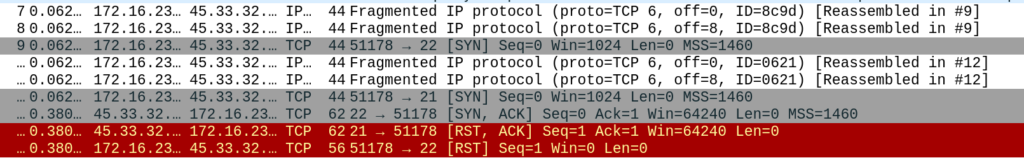
Note: You can combine the switch –mtu (must be a multiple of 8) which specifies the maximum transmission unit size.
4. Source Port Scan
In some situations, the target is configured to accept incoming traffic from certain ports such as dns (53) or http/https (80/443).
Nmap has the ability to change the source port when scanning by specifying the –source-port (-g) switch.
sudo nmap -Pn -n <Target-IP> -p 21,22 --source-port 53 --disable-arp-ping --packet-trace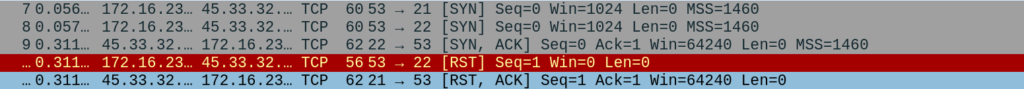
III. Conclusion
Firewall evasion is an art which requires research, analysis, various of techniques in combination and even trial and error in order to bypass successfully. Please remember that, to defeat the enemy we first must understand them.