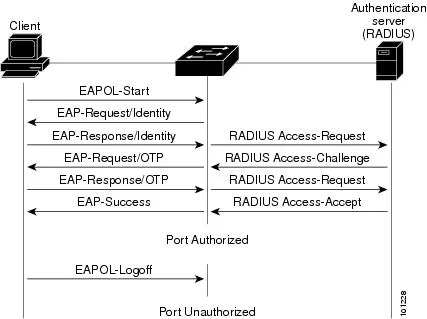
I/ 802.1X Port-based Network Access Control (PNAC) enables authentication of devices that connect to a local network. The below image illustrates the transmission of Extensible
Tag: Usernames
Internal Network Attack Vector Discovery (Part I)
Most of the protocols using the data link layer and local broadcast addresses are nonroutable, which means you can only evaluate them from the local
TLS Security (Final) – Assessment
In this blog, we will go over some of the methods and tools to assess the TLS security posture during an engagement. Please remember to
TLS Security (Part II)
I. Understanding TLS Vulnerabilities Hackers can exploit some TLS flaws remotely, but practical exploitation of many requires network access to compromise ciphertext and data injection.
TLS Security (Part I)
I. What is TLS? Before getting into TLS security, let’s first talk about encryption. It can generally be applied at different levels, from encryption in
SECURITY FEATURES on MacOSX (Final)
We’ll go over the remaining security features on macOSX in this blog. 9. Firewall There is a built-in standalone firewall on MacOSX but it’s not
LAN MANAGER / NT LAN MANAG & NTLMv2 Hashes
Windows LM or NTLM & NTLMv2
OSINT & Passive Recon
In this blog, we’ll look at what OSINT – Open Source Intelligence is and tools we can use to gather information about the target. Reconnaissance
How to Secure WordPress Part III
Let’s carry on where we left off last week (Part I and Part II). II. Secure Important Components 16. WordPress Security Keys & Salts WordPress
How to Secure WordPress Part II
Welcome to the next of the securing WordPress series. We’ll continue where we left off in part I. Secure WordPress Components (Contd) II. Secure Important