I. What is TLS? Before getting into TLS security, let’s first talk about encryption. It can generally be applied at different levels, from encryption in
SECURITY FEATURES on MacOSX (Final)
We’ll go over the remaining security features on macOSX in this blog. 9. Firewall There is a built-in standalone firewall on MacOSX but it’s not
SECURITY FEATURES on MacOSX (Part II)
In this blog, we’ll continue where we left off which covers the remaining security features on MacOS. 4. Automatic Updates New vulnerabilities for operating systems
SECURITY FEATURES on MacOSX (Part I)
In this blog, we will go over some of the security features on MacOS that implemented by Apple to protect their users. Apple is known
SHODAN For PENETRATION TESTER
In this blog, we will talk about how we can use one of the most commonly used search engines during the penetration testing process –
LAN MANAGER / NT LAN MANAG & NTLMv2 Hashes
Windows LM or NTLM & NTLMv2
OSINT & Passive Recon
In this blog, we’ll look at what OSINT – Open Source Intelligence is and tools we can use to gather information about the target. Reconnaissance
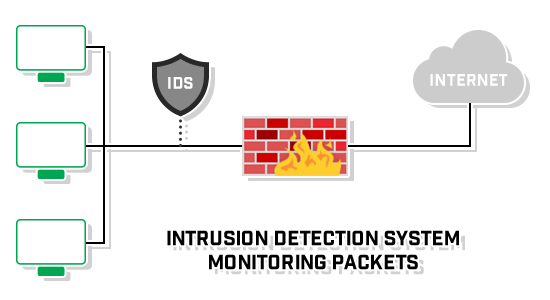
Introduction to IDS and IPS
An IDS or Intrusion Detection System monitors activity that is known or suspected to be malicious in its intent, raising alerts to a security or SOC teams to be analyzed.
IPS or Intrusion Prevention System adds another layer of defensive measure to protect resources.
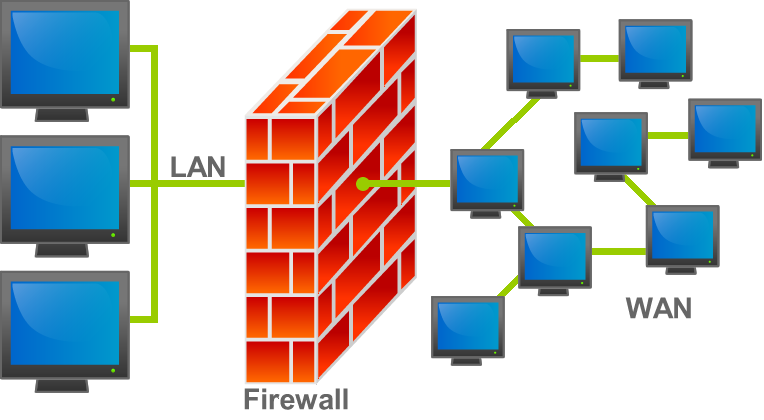
Firewalls Introduction
Firewalls can handle simple attacks pretty quickly. However, they can easily be tricked because of the nature of network traffic in which almost all network traffic is bi-directional, but stateless firewalls must decide on….
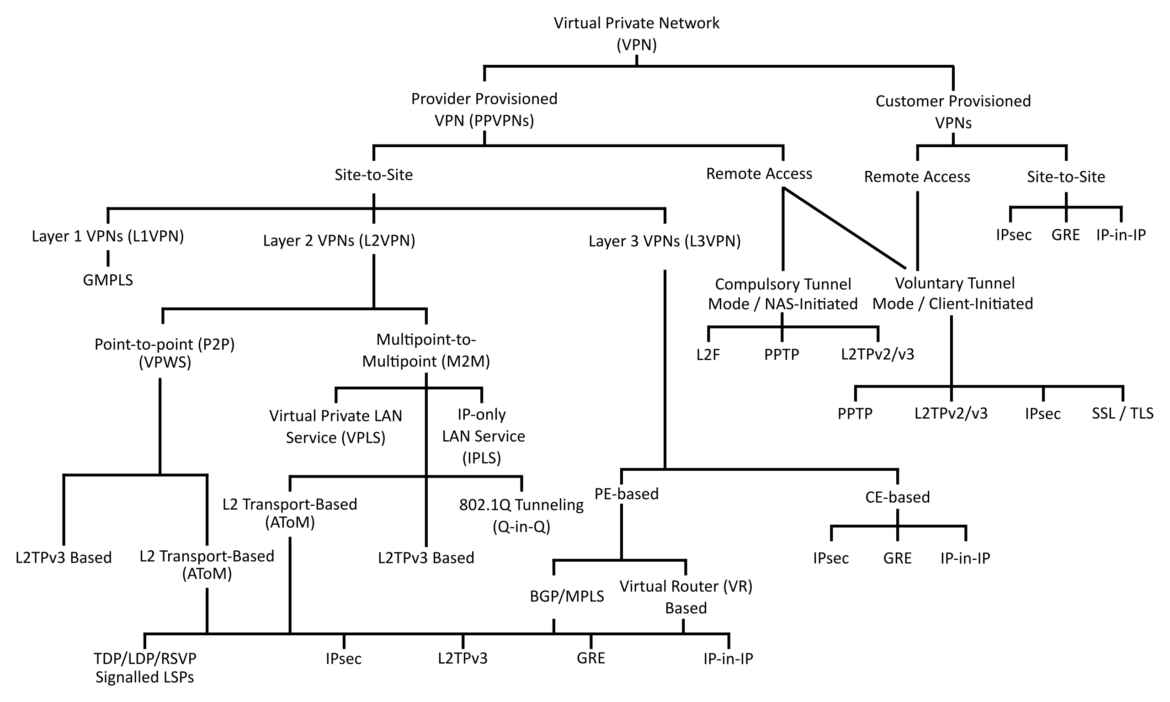
Data Security Part I
In this blog, we’ll discuss the concept of VPN, in transit encryption and what benefits VPN bring to us. I. High Level Overview of VPN