Windows LM or NTLM & NTLMv2
Category: Network
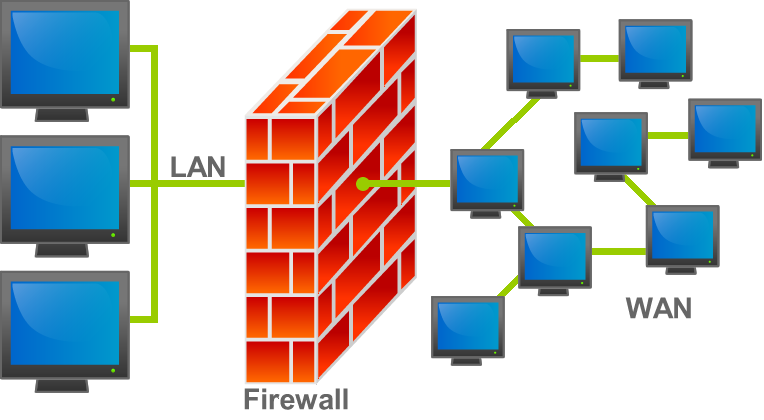
Firewalls Introduction
Firewalls can handle simple attacks pretty quickly. However, they can easily be tricked because of the nature of network traffic in which almost all network traffic is bi-directional, but stateless firewalls must decide on….
How to Secure WordPress Part IV
Following the Part III, in this blog post, we’ll go over the security checklist that can be used as a reference to enhance the security
How to Secure WordPress Part III
Let’s carry on where we left off last week (Part I and Part II). II. Secure Important Components 16. WordPress Security Keys & Salts WordPress
How to Secure WordPress Part II
Welcome to the next of the securing WordPress series. We’ll continue where we left off in part I. Secure WordPress Components (Contd) II. Secure Important
How to Secure WordPress Part I
I. Introduction When people talk about WordPress, often it would be something like: “it’s unsecured, it’s easy to get hacked,…”. But those are just misconceptions.
Common Network Attack Vectors
Today we are going to talk about a few common attack vectors, which are often taken when performing network penetration testing in enterprise and business