Understanding GPO Hierarchy and Workflow: Discover how Group Policy is processed in Windows environments. Learn the GPO hierarchy—Local, Site, Domain, and OU—and how each level
Category: Network
Group Policy Introduction (Part I)
A Core Tool for Secure IT ManagementDiscover the fundamentals of Group Policy in Windows—what it is, how it works, and why it’s essential for centralized
Internal Network Attack Vector Discovery (Part III)
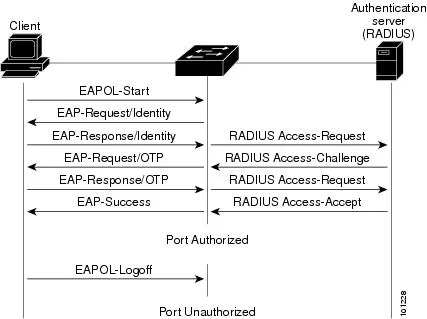
I/ 802.1X Port-based Network Access Control (PNAC) enables authentication of devices that connect to a local network. The below image illustrates the transmission of Extensible
Internal Network Attack Vector Discovery (Part II)
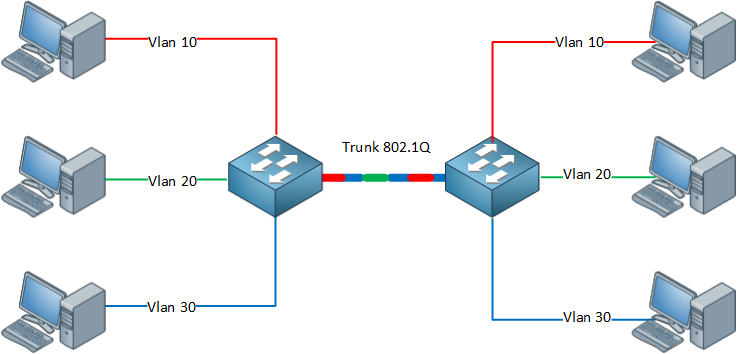
802.1Q VLAN VLANS are used within enterprises to segment networks and create individual broadcast domains. Along with reducing unnecessary broadcast of traffic, 802.1Q tagging limits
Internal Network Attack Vector Discovery (Part I)
Most of the protocols using the data link layer and local broadcast addresses are nonroutable, which means you can only evaluate them from the local
TLS Security (Final) – Assessment
In this blog, we will go over some of the methods and tools to assess the TLS security posture during an engagement. Please remember to
TLS Security (Part I)
I. What is TLS? Before getting into TLS security, let’s first talk about encryption. It can generally be applied at different levels, from encryption in
SECURITY FEATURES on MacOSX (Final)
We’ll go over the remaining security features on macOSX in this blog. 9. Firewall There is a built-in standalone firewall on MacOSX but it’s not
SECURITY FEATURES on MacOSX (Part II)
In this blog, we’ll continue where we left off which covers the remaining security features on MacOS. 4. Automatic Updates New vulnerabilities for operating systems
SECURITY FEATURES on MacOSX (Part I)
In this blog, we will go over some of the security features on MacOS that implemented by Apple to protect their users. Apple is known