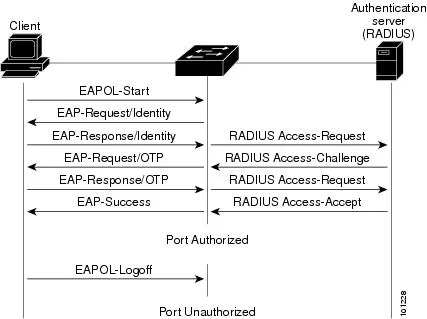
I/ 802.1X Port-based Network Access Control (PNAC) enables authentication of devices that connect to a local network. The below image illustrates the transmission of Extensible
Category: Attack Vector
Internal Network Attack Vector Discovery (Part II)
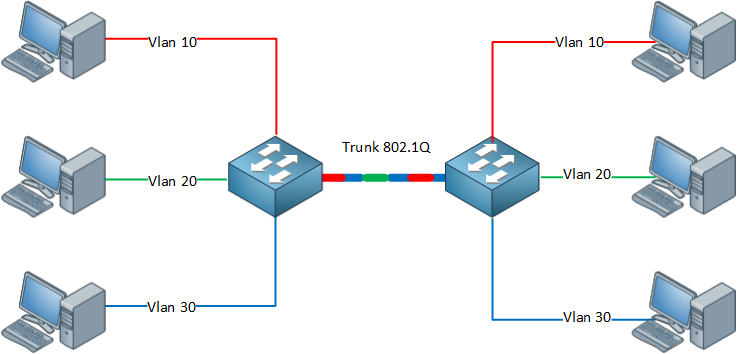
802.1Q VLAN VLANS are used within enterprises to segment networks and create individual broadcast domains. Along with reducing unnecessary broadcast of traffic, 802.1Q tagging limits
Internal Network Attack Vector Discovery (Part I)
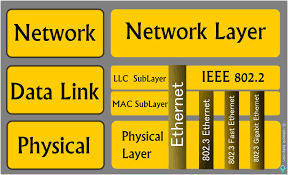
Most of the protocols using the data link layer and local broadcast addresses are nonroutable, which means you can only evaluate them from the local