Windows memory management is a critical part of how the operating system maintains stability, performance, and security. In this second part of the Windows Fundamentals series, we’ll explore the differences between user memory and kernel memory, and break down the core components that shape how Windows handles system memory.
User Memory vs Kernel Memory
Windows (on a 32-bit system) supports up to 4 GB of virtual memory. This address space is typically divided equally:
- 2 GB for user-mode applications
- 2 GB for kernel-mode operations
This structure ensures kernel memory remains accessible system-wide, independent of the active process, while also remaining secure from user-mode access.
Because of this split, applications can only access a 31-bit address space, as the most significant bit is always 0. Any 32-bit address beginning with a hexadecimal value of 8 or higher is likely invalid in user mode—a useful detail for reverse engineering and debugging.
Inside the Kernel Memory Space
The kernel memory space houses all the essential system components and services. Although the allocation is mostly static, its size can be influenced by physical memory availability and certain registry configurations.
Let’s explore the main areas inside kernel memory.
- Paged and Non-Paged Pools
Windows provides two special kernel-mode heaps:
- Paged Pool: Memory that can be swapped to disk. It’s used for less time-critical data.
- Non-Paged Pool: Memory that cannot be paged out. It’s always present in RAM, making it crucial for drivers and core system operations.
These memory pools are used by all kernel components and device drivers.
2. System Cache
The system cache is managed by the Windows Cache Manager. It stores actively used files in memory to minimize disk access.
When a file is opened:
- A section object is created
- It’s mapped into the system cache space
- File operations like
ReadFileorWriteFileaccess this cache, using APIs such asCcCopyReadorCcCopyWrite
This mechanism significantly boosts performance.
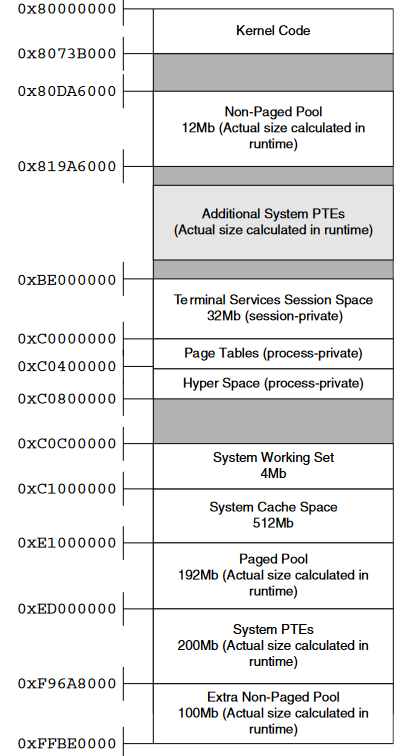
3. Terminal Services Session Space
To support multiple user sessions via Remote Desktop or Terminal Services, Windows introduces session-specific memory:
- Each session has its own instance of
WIN32K.SYS - Loaded into the same virtual address, but within a different session space
- A Session Pool (session-private paged pool) is included for session-specific data
This allows multiple GUI sessions to run in parallel without interference.
Advanced Kernel Memory Components
4. Page Tables and Hyper Space
Windows reserves memory for process-specific data like:
- Page Table Area: A virtual view of the currently active page tables
- Hyper Space: Primarily maps the working set of the current process
Both are vital for handling virtual-to-physical memory translations efficiently.
5. System Working Set
The system working set tracks the usage of pageable kernel memory. It plays a key role in managing memory for:
- Paged pool
- System cache
By keeping tabs on active memory pages, the system ensures optimal memory distribution and reduces performance bottlenecks.
6. System Page-Table Entries (System PTE)
The System PTE space is not a traditional heap. Instead, it provides virtual memory regions for:
- Mapping large driver allocations
- Storing kernel stacks (each thread gets one)
- Mapping device driver executables
Developers can allocate System PTEs using the MmAllocateMappingAddress kernel API.
Conclusion
Understanding the structure and purpose of Windows kernel memory is essential for system developers, security researchers, and IT professionals. From paged pools to session space and cache management, each component plays a role in how Windows maintains efficiency and security.
As we move further into Windows internals, mastering kernel memory will help you in tasks like:
- Debugging and reverse engineering
- Driver and OS-level development
- Performance tuning and memory diagnostics
Stay tuned for more deep dives in our Windows Fundamentals series.
🖥️ Windows Fundamentals (Part I): Understanding Memory Management in Windows
