In this blog, we’ll discuss the concept of VPN, in transit encryption and what benefits VPN bring to us.
I. High Level Overview of VPN
First let’s talk about network layer encryption which protects network conversations, whether the application using the network supports cryptography or not. Network layer encryption sits in between the sender and receiver. It accepts in clear-text information and then encrypts it prior to sending it out. At the receiving end, the information is decrypted and forwarded on to its final destination. Virtual Private network (VPN) works the same way to provide end-to-end encryption.

II. Different Type of Network Encryption
- Private Network
This type of networks require infrastructure provided by a 3rd party (such as telecommunications provider) in order to be connected together. How that infrastructure was view in the past (from a security perspective) is very different from how it would be viewed today in which in the past. Even though the 3rd party telco would have the technical ability to intercept network communications as it transits between the disparate LANs, the telco was not considered (for most) to be in the threat matrix.
In fact, not only was the telco considered to be in a threat category, organizations would go so far as to refer to the connections provided by the telco as being private. The reason for such is simple, a telco would, in essence, provide a connection for our disparate LANs which was reserved for our exclusive use, and the sense of exclusivity gave us a sense of privacy.
These connections are often referred to as private lines, or leased lines. Leased lines are quite beneficial in that there is a way to connect disparate LANs together without an organization having to install the necessary infrastructure itself. However, on the downside, leased lines are pretty expensive, invoiced on a monthly basis, and the amount we pay increases as the distance between the LANs also increases.
Because of all that, led to the development of the term private network. With a concept of private being applied to such connections, it isn’t surprising that organizations weren’t concerned with providing any confidentially protection for their traffic as it transited between networks, even though the telco was in a position for interception.
There’s another term called MPLS (Multiprotocol Label Switching) that is the same concept as leased lines.
Many organizations today still rely on such infrastructure when other options such as using a connection to the internet is not considered sufficient for their purposes. The only thing new today is that how we perceive the telco that regardless of how unlikely it would be for a telco to be malicious, we do consider a telco as being a potential threat, and, as such, we will want to consider for the confidentiality of data in transit as it moves between our LANs.
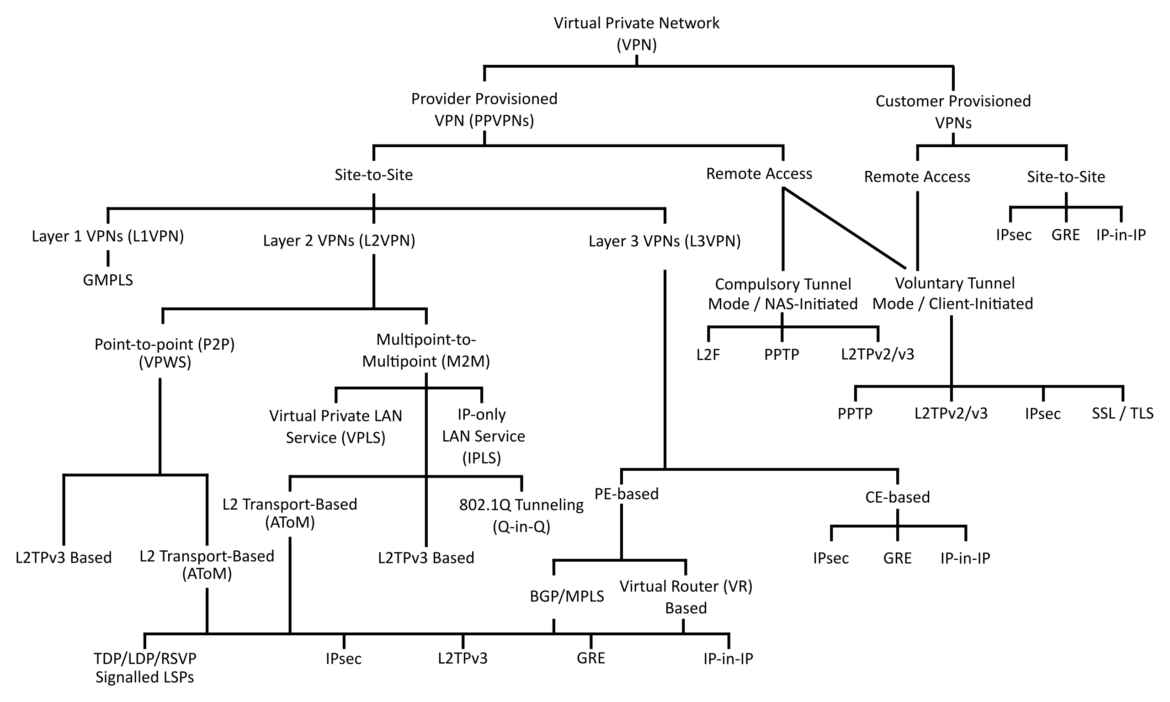
2. Virtual Private Network (VPN)
A VPN is nothing other than a concept of end-to-end protected network communication, whereby that communication is sent over an untrusted network infrastructure. It’s is a virtual network that can operate on top of any underlying network infrastructure and is a capability that can be leveraged over leased lines, or any other private network concept, just as it can over the internet.
Because leased lines, and other private network connections, tend to be incredibly expensive, organizations that could not afford such infrastructure but still required the ability to connect multiple LANs together needed another, less expensive option.
a. Advantage
One of the biggest advantages of VPN technology is its flexibility. After you have all the components to establish a VPN, setting one up requires only configuration. This makes the technology far more flexible than private circuits, which must be ordered far in advance of their use and might also require additional hardware.
b. Pros and Cons
- Pros:
- Connect easily and cheaply to the internet
- Create two internet connection points
- Encrypt traffic over the internet
- A lot more bandwidth
- VPNs are ideal for file transfers, email,…
- If time is not critical, VPNs can save a lot of money
- Cheaper
- Cons
- VPNs are not ideal for financial, medical, and other real-time operations
- Don’t get dedicated bandwidth across the internet
- Onely 1-2 seconds delay compared to private network
- Can be critical for some operations
III. Types of Remote Access
1. Site-to-site VPNs
Provide connectivity to networks, such as headquarters and a remote office. In these connections, gateway devices are located in front of both networks. Information needing to flow between the sites is directed to the local gateway, which then encrypts the contents of the message and forwards it to the other site’s gateway. The remote site’s gateway decrypts the message and then sends it onto its internal destination.
2. Client-to-site VPNs
Provide remote access from a remote client, such as working from home or travelling employee to the corporate network. Such VPNs are normally established between the client’s computer and a gateway device located at the border of the corporate network. The client’s computer will use a VPN client that allows it to establish the connection to the VPN gateway.
3. Client-to-client VPNs
Establish a protected link between two specific computers. As such, they could be considered the most secure of the VPN types because in the client-to-site and site-to-site VPNs, part of the path between the sender of a message and the receiver of the message in unencrypted. For instance, in client-to-site VPNs, the communication from the client’s computer to the VPN gateway is protected, but the message travels unencrypted (and unprotected) from the VPN gateway to the internal corporate computer the client is trying to communicate with. If an attacker inserts themself somewhere between the VPN gateway and the destination computer, they would be able to eavesdrop on or modify the contents of the message.
Even though the client-to-client VPNs are more secured but not implemented often. The reason given was because of the required configuration in which each pair of hosts wanting to communicate must be specifically configured to allow the communication. The most important part of this configuration lies in key installation. Each host must have a separate unique key that it can use to encrypt information to a particular destination host. Because of this, client-to-client VPNs between every two hosts would quickly become unmanageable as the number of hosts increases, if manual configuration is used. Public key infrastructure (PKI) is one way to address this key distribution problem.
Part II, Secure WordPress Series